Resource Hub
Featured Resources
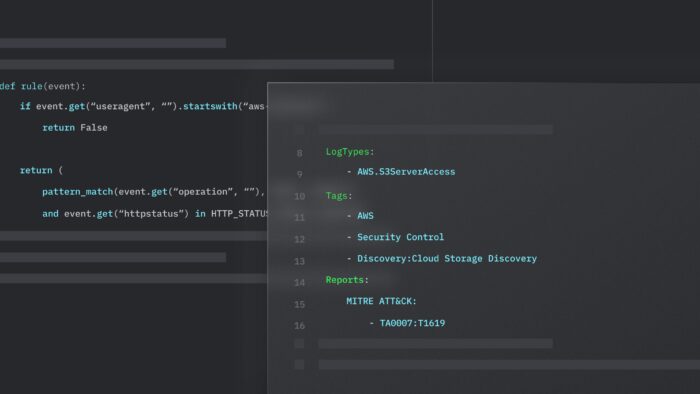
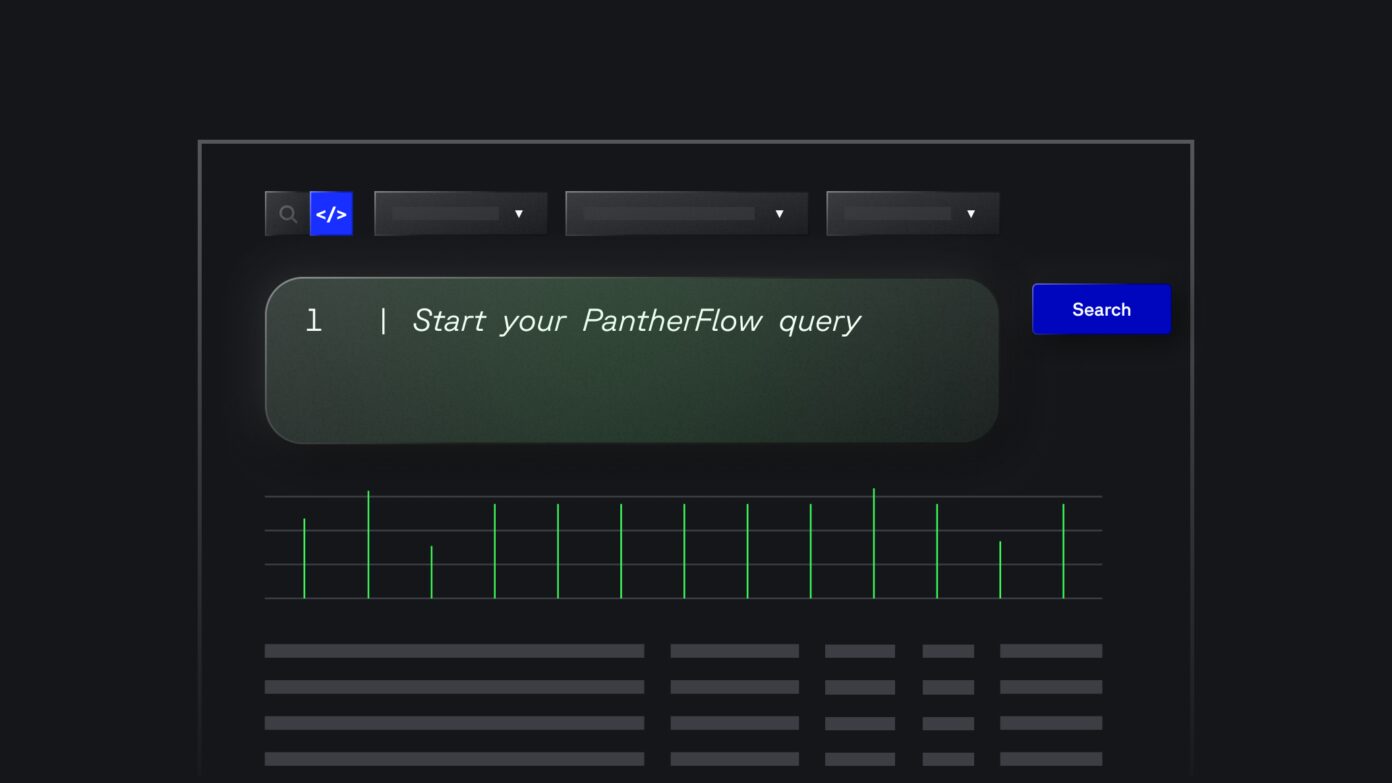
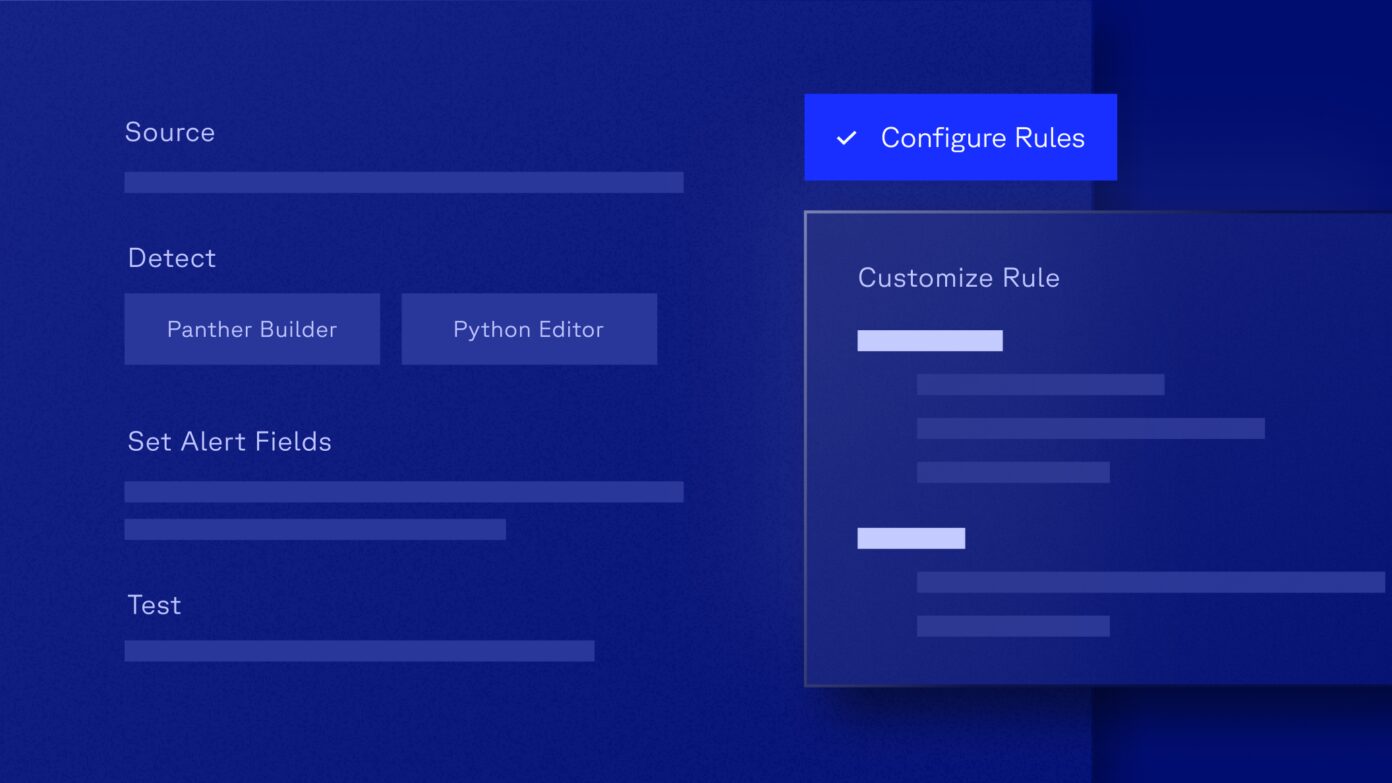
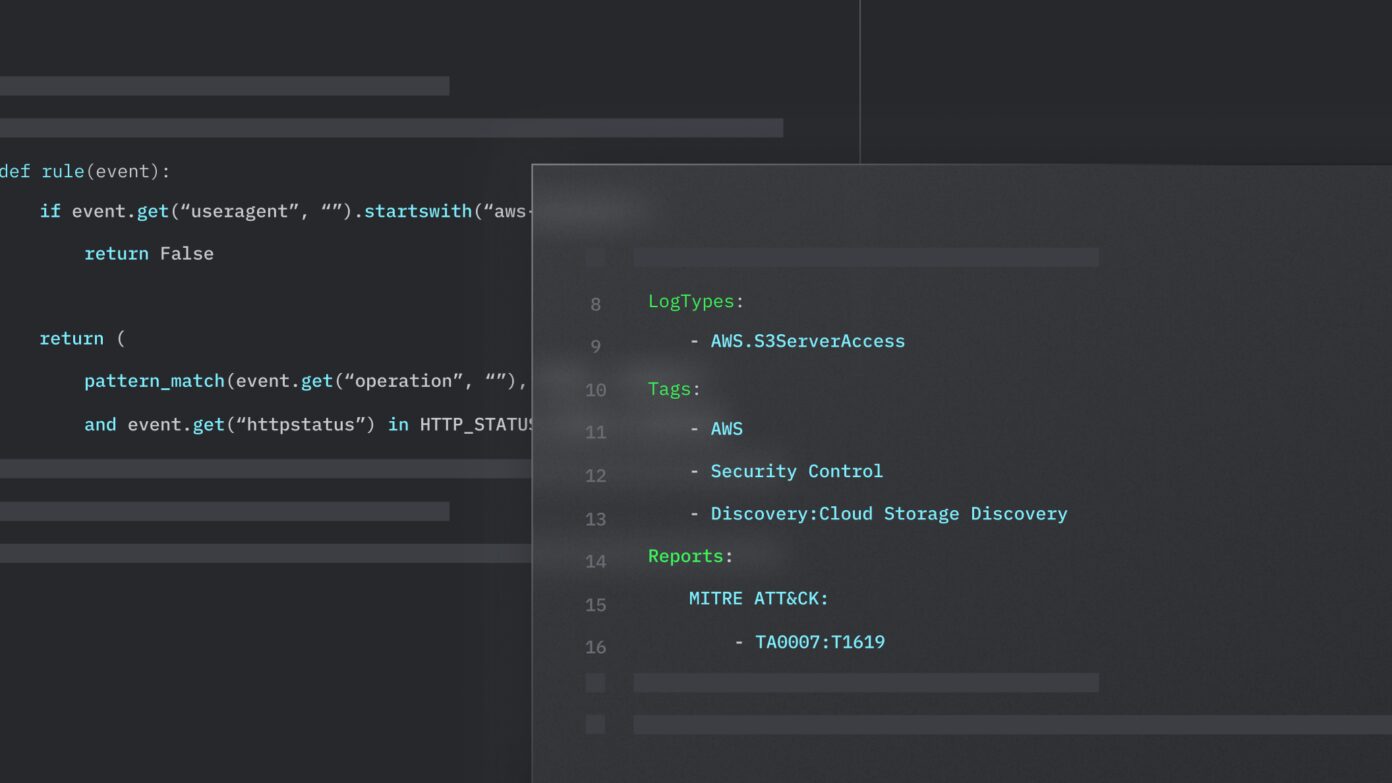
Detection-as-Code
All Resources
Blog
Introducing the Panther Sigma Rule Converter
Case Study
How Jumio Streamlined Data Onboarding and Built High-Fidelity Alerts with Panther

Case Study
Financial Services Lean Security Team Offsets Head Count with Panther’s Streamlined SecOps

Case Study
Asana Uses Engineering Principles to Automate Detection and Response Workflows with Panther

Podcast
AppOmni’s Drew Gatchell on Creating Better Detection for SaaS Platforms

Blog
How to Evaluate a Security Detection Platform

Podcast
Block’s Emanueal Mulatu on Reducing Burnout, Fostering Engagement, and Increasing Productivity in Security

Blog
How to Create a Code-Based Detection